Vendor-related security risks are rapidly increasing, putting organizations under pressure to bolster their defenses. However, traditional assessment methods are falling short, leaving many companies vulnerable. A new blueprint from Info-Tech Research Group introduces a risk-based vendor security assessment framework designed to address these evolving threats.
Why Traditional Vendor Security Assessments Fall Short
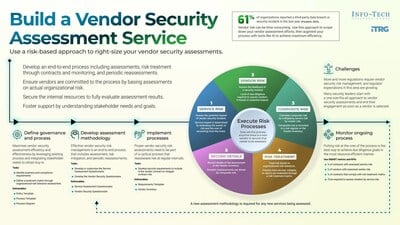
Many organizations use one-size-fits-all vendor security assessments that often create more problems than they solve. Outdated processes can overwhelm security teams, frustrate stakeholders, and slow down critical business operations. As regulations become stricter and third-party breaches grow more common, these blunt methods leave businesses exposed. Sometimes, vendor assessments are so complex that vendors decline to participate, or internal teams try to avoid the process entirely, increasing organizational risk.
Info-Tech’s New Risk-Based Vendor Assessment Framework
Info-Tech Research Group now offers a comprehensive framework for risk-based vendor security assessment. Their blueprint, “Build a Vendor Security Assessment Service,” empowers IT leaders to focus on what truly matters. The structured approach includes:
- Defining governance and process: Set organizations up for success by clarifying rules, responsibilities, and policies aligned with risk tolerance.
- Developing an assessment methodology: Create targeted, efficient risk questionnaires as opposed to lengthy, generic surveys.
- Implementing and monitoring: Establish a feedback loop that adapts security requirements and ensures continuous reassessment.
By personalizing each assessment to actual business risk, companies improve compliance and make more informed decisions.
Implementing a Continuous Approach to Vendor Risk Management
Info-Tech’s guidance emphasizes continuous improvement and ongoing risk monitoring rather than relying on static, one-off checks. The recommended process includes:
- Evaluating service risk by measuring potential impacts and associated recovery costs.
- Assessing vendor risk to determine the likelihood of a security incident.
- Calculating a composite risk score to prioritize threats according to actual exposure.
- Applying risk treatment strategies like accepting, mitigating, or rejecting risks as needed.
- Recording outcomes and adjusting reassessment schedules based on evolving risk profiles.
This approach not only reduces risk exposure but also allows for better alignment between stakeholders and stronger vendor accountability.
In summary, Info-Tech Research Group’s risk-based approach transforms vendor security assessments from administrative burdens into strategic defenses. By focusing on real risks, streamlining assessments, and emphasizing continuous improvement, organizations can reduce vulnerabilities and enhance operational efficiency. As the cybersecurity landscape evolves, adopting smarter, more adaptable vendor security assessment practices has never been more critical.
Don’t miss our latest Startup News: Cambium Networks Delivers Game-Changing Wi-Fi Boost for Hotels