In the ever-evolving landscape of cybersecurity, perimeter defenses are no longer sufficient. As enterprises embrace hybrid work models, Info-Tech Research Group presents a vital resource designed to fortify organizations against emerging threats using the zero trust security model. This blueprint offers strategies that navigate away from traditional security perimeters, focusing instead on securing identities, devices, and data wherever they may reside.
Zero Trust Security: An Essential Strategy
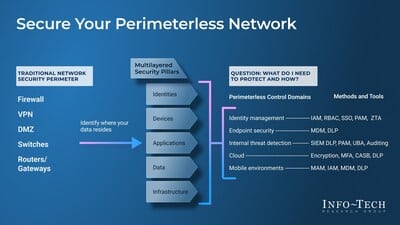
The concept of zero trust pivots on the assumption that threats can exist both inside and outside traditional network boundaries. Therefore, Info-Tech’s latest blueprint, Secure Your Perimeterless Network, advocates for a comprehensive approach that does not inherently trust any entity. Instead, it verifies each one attempting to connect to the system, regardless of location. “Security should focus on identities, data, and applications rather than enclosing them within a conventional perimeter,” explains John Donovan, principal research director at Info-Tech Research Group.
Addressing Challenges in Perimeterless Networks
Adopting the zero trust model in a perimeterless environment presents notable challenges, including the transition from legacy IT systems and fostering familiarity with new security technologies. The Info-Tech blueprint emphasizes the importance of overcoming cultural resistance and enhancing interoperability among complex systems. It points out that organizations must manage cloud integrations and data silos effectively, ensuring they do not hinder the new security measures.
Implementing Zero Trust: Key Control Areas
To operationalize zero trust, Info-Tech advises focusing on several critical control areas within the IT landscape. These include:
- Identities: Ensuring users have secure identities with proper roles and access controls such as multifactor authentication and single sign-on.
- Devices: Implement endpoint protection and precisely defined access privileges.
- Applications: Segment applications by workflow and restrict administrative access.
- Infrastructure: Install robust monitoring and set up timely alerts.
- Network: Treat the internal network as a neutral zone where the absence of implicit trust is a norm.
- Data: All data should be encrypted both in transit and at rest, with strict policies regulating access and usage.
This strategic guidance ensures that each element contributes to a secure and resilient zero trust architecture.
In summary, Info-Tech Research Group’s blueprint for implementing a zero trust security model provides a strategic roadmap for organizations worldwide. By focusing on identity, device, and application security, enterprises can effectively manage and mitigate risks within perimeterless and hybrid environments. As cyber threats evolve, the adoption of these resilient strategies becomes increasingly critical for maintaining robust cybersecurity defenses.
Don’t miss our latest Startup News: Iconic Transforms M&A Landscape with Key Acquisition