In the face of increasing unauthorized access threats, Info-Tech Research Group has released a detailed blueprint to transform identity and access management (IAM) systems. This new strategy, aimed at bolstering digital security and regulatory compliance, provides a four-step, research-backed framework to modernize IAM systems, fortifying them against current and future cybersecurity challenges.
Overview of Info-Tech’s IAM Blueprint
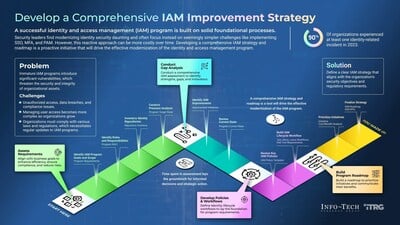
The recently unveiled blueprint by Info-Tech Research Group stresses a comprehensive approach are paramount for enhancing organizational security and efficiency. Michel Hébert, principal research director, emphasizes the critical nature of developing resilient IAM systems through innovative solutions like decentralized identity and a clear roadmap for integration. The blueprint not only addresses pressing security concerns but also caters to the complexity and scalability needed for large and evolving IT environments.
Key Steps in IAM Strategy Enhancement
Info-Tech outlines a strategic four-step process to solidify IAM frameworks:
- Assess Requirements: Align IAM goals with business objectives to improve efficiency and compliance, and minimize risks.
- Conduct Gap Analysis: Identify strengths and opportunities within the current IAM setup.
- Develop Policies & Workflows: Create identity lifecycle workflows and program requirements.
- Build Program Roadmap: Prioritize initiatives and clearly communicate their benefits to stakeholders.
By following these steps, organizations can anticipate a boost in security and overall business alignment.
Benefits of a Proactive IAM Approach
Adopting a proactive approach in IAM modernization allows for more than just addressing single-point solutions like multi-factor authentication or privileged access management. It enables the creation of systems that are robust, scalable, and adaptable to new technologies. Info-Tech’s blueprint ensures organizations are equipped to handle dynamic access needs and compliance requirements, ultimately enhancing operational efficiency and reducing vulnerabilities.
This elaborative blueprint from Info-Tech serves as a vital resource for security leaders aiming to revamp their IAM strategies effectively. By laying out the complexities of modern cybersecurity and providing actionable steps for improvement, Info-Tech not only aids in fortifying security postures but also ensures that these improvements are aligned with broader business goals. The comprehensive nature of this strategy marks a significant step toward safeguarding digital assets in an ever-evolving threat landscape.
Don’t miss our latest Startup News: Ambilight Shines at CES 2025 with Smart-Tech Innovations